EDR: What It Is and Why You Need ItEDR: What It Is and Why You Need It
EDR is a key supplement to your endpoint protection and managed detection and response platforms.
March 19, 2021

Sponsored by Kaspersky
There’s a lot of noise in the market right now about how endpoint detection and response (EDR) is the Next Big Thing. But what exactly is EDR? Gartner1 describes it like this: “EDR tools provide a method for security and risk management technical professionals to answer two key questions about the security of their environment: What happened here? [and] What is happening right now?”
What does this mean in practice, and why is it so important for organizations to supplement their endpoint protection platform (EPP) with EDR tools and/or managed detection and response (MDR)?
What Is EDR?
Let’s take a closer look. In recent years, cybercriminals have been focusing more and more on evasive threats specifically designed to bypass existing endpoint protection measures. (This is as opposed to commodity threats, which are relatively easy for EPPs to detect and prevent.)
One reason for this is that it’s becoming much easier–and cheaper–for cybercriminals to find, combine and test ready-made tools and methods (including “rent-a-malware”campaigns with 24/7 support). In addition, these kind of attacks promise a much higher chance of success than traditional scenarios.
Add to this the surge in remote working that is dissolving the corporate perimeter for many organizations, and it’s easy to see why endpoints will remain on the frontline in the battle against cybercriminals for the foreseeable future.
So what happens when an EPP is confronted by an evasive cyberthreat? These threats are hard to detect due to the range of evasion techniques being adopted–particularly the use of legitimate and system-native tools. And by staying undetected for longer, they also have the time needed to explore and entrench themselves in a business’s infrastructure and cause more damage–be it a data breach, a ransomware or spyware attack or directly overriding operations.
The result? The average financial impact of a data breach2 is $101,000 for SMBs and $1.09 million for enterprises. And the slower the response, the larger the average impact, which rises to $118,000 and $1.34 million, respectively (32% more for enterprises!), for responses taking longer than a week.
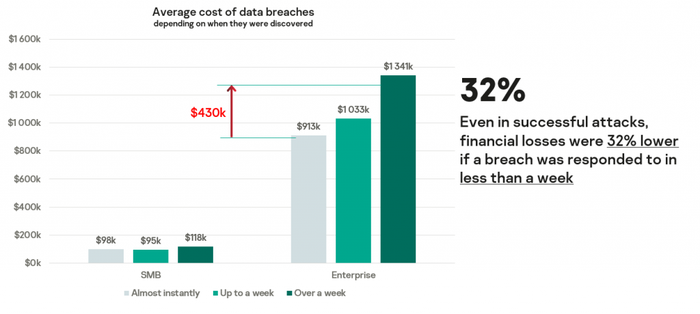
With this kind of impact, maybe businesses shouldn’t be asking why they should invest in EDR, but why they haven’t already done so.
What EDR Will Do for You
So what will EDR do for you if, and when, you go for it? In simple terms, every time you receive an alert, EDR will help you to understand where the threat came from, how it developed, its root cause, whether it touched any other hosts and its full scale.
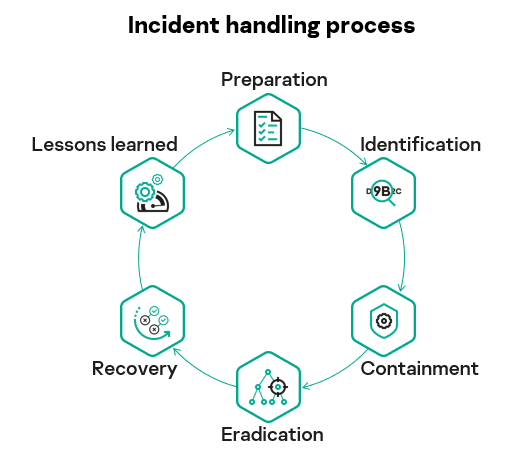
It can also guide you through a simple incident handling process, including identification, containment, eradication and recovery, as well as analyzing lessons in order to help prepare for future attacks. For example:
What did the EDR tool find? Is it a common or a serious threat, and, based on the context and details of the threat and the incident it created, is a response required?
What needs to be done about the threat? Isolate the host? Prevent execution? Quarantine suspicious files?
Run an indicator of compromise (IoC) scan to find and delete related files, along with any other processes needed to eradicate the threat.
Return the network to normal. For example, if an infected host was isolated to prevent the spread of infection, this can be taken back out of isolation.
Analyzing lessons learned. May involve integrating IoC data with existing security tools, reviewing access and web controls, or blocking access to particular IP addresses or email accounts. This would also be a good time to review the security awareness levels within your organization.
Whether you use an in-house EDR tool and/or MDR, working together with your EPP your solutions should block a large number of threats automatically. And, when incidents occur, you can investigate them more effectively. This means gaining more insight into what’s going on behind the scenes to get a better understanding of the threats you’re seeing, and being able to respond to them quickly and easily. You can also look for other devices that may also have been comprised, further strengthening your security posture especially in relation to new, unknown and evasive threats.
Whether you want to strengthen your internal defenses or combat the latest threats with expert external guidance, Kaspersky can help. Our cloud-enabled Kaspersky Optimum Security lets you upgrade your protection against new, unknown and evasive threats, through effective threat detection and response and 24/7 security monitoring, without prohibitive costs or complexity.
Learn more at go.kaspersky.com/optimum
1 Gartner – Solution Comparison for Endpoint Detection and Response Technologies and Solutions – Jan 2020
2 Kaspersky – IT Security Economics 2020
This guest blog is part of a Channel Futures sponsorship.
Read more about:
MSPsAbout the Author
You May Also Like


