Purdue University Launches Open Source, All-in-One Network Forensics ToolkitPurdue University Launches Open Source, All-in-One Network Forensics Toolkit
FileTSAR is free to law enforcement agencies, available for fee to other organizations including MSSPs.
March 6, 2020

Purdue University has introduced an all-in-one toolkit for law enforcement and companies to use to track down cybercriminals, stop insider threats, and to stop other abuses conducted via technology and moved over a network. Cybersecurity experts at Purdue collaborated with law enforcement agencies throughout the U.S. to develop the toolkit.
The Purdue Toolkit for Selective Analysis and Reconstruction of Files (FileTSAR) includes in one complete package the top open-source investigative tools used by digital forensic law enforcement teams. (Provided by Purdue University)
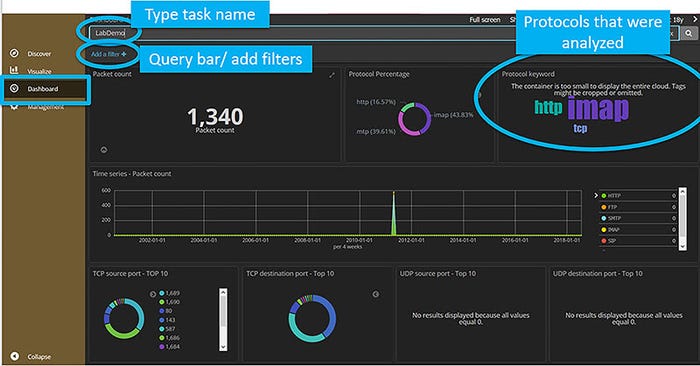
The toolkit is called FileTSAR, an acronym for Toolkit for Selective Analysis & Reconstruction of Files (FileTSAR). The project was funded by the National Institute of Justice and is free to law enforcement agencies for three years. Organizations in the private sector can also use the toolkit for a fee.
Following the larger software industry trend of avoiding proprietary software, this toolkit is comprised entirely of open-source software. FileTSAR is considered an all-in-one package because it contains the best of the open-source investigative tools used by digital forensic law enforcement teams at the local, state, national and global levels.
“FileTSAR allows forensic investigators to capture, selectively analyze and reconstruct files from network traffic,” said Kathryn Seigfried-Spellar, an associate professor of computer and information technology in the Purdue Polytechnic Institute, who helps lead the research team.
“The main functions of this tool are capturing data flows and providing a mechanism to selectively reconstruct documents, images, email and VoIP conversations,” Seigfried-Spellar added.
The toolkit can be used to uncover network traffic to track cybercriminals, discover employees sending out trade secrets or other sensitive information, or to recreate incriminating conversations or activities by employees or outside activities. In short, it’s a cyber forensics toolkit.

Kathryn Seigfried-Spellar, an assistant professor in the Purdue Polytechnic Institute’s Department of Computer and Information Technology, works on a computer in the Tippecanoe County High Tech Crime Unit in Discovery Park. (Purdue University file photo/Rebecca Wilcox)
“Knowing that we created an affordable tool that will help law enforcement with their network forensic investigations is incredibly rewarding,” Seigfried-Spellar said.
More than 100 law enforcement agencies have requested the technology thus far, and the final count is expected to rise much higher.
MSSPs working with clients in law enforcement need to be aware of the toolkit and its high adoption rates in order to integrate it with other tools the MSSPs sell to or use in behalf of these clients. Additionally, it is prudent for MSSPs to consider this toolkit for use by or for their client organizations in the private sector. While the toolkit is not free for organizations outside of law-enforcement agencies, it is being billed as affordable to all. An affordable price adds to the toolkit’s overall attractiveness as a comprehensive forensic tool.
However, specific pricing information was not publicly available as of this writing. Law enforcement agencies and other interested parties can learn more specific information about licensing and gain access to the toolkit via the Purdue Research Foundation Office of Technology Commercialization (OTC).
Read more about:
MSPsAbout the Author
You May Also Like


