How MSSPs Can Support Risk-Based Patch Management
Tailor alerts to customers' needs for more effective patch management.


Ayesha Prakash
The growing interest in managed security service providers (MSSPs) presents ample opportunity. But as I noted in March, providers must understand the cybersecurity challenges their customers face to succeed under an MSSP model. From an outsider’s perspective, understanding how to help customers navigate an ever-changing cyber threat landscape can feel like a daunting task. So today, let’s just focus on one area where customers are in continuous need of support: patch management.
BlueKeep: The Next EternalBlue?
In light of concerns over the BlueKeep vulnerability and two similar remote desktop protocol (RDP) vulnerabilities disclosed on Aug. 13, it’s more important than ever for MSSPs to recognize the critical importance of empowering customers with the tools they need to make effective patching decisions. BlueKeep (CVE-2019-0708) is a flaw in the Windows RDP protocol used by admins for remote administration. Many security researchers worry BlueKeep has the potential to echo the havoc wrought by a Microsoft SMB vulnerability targeted by the EternalBlue exploit.
EternalBlue was used in the large-scale WannaCry and NotPetya cyberattacks in 2017. A patch for the vulnerability exploited by WannaCry (CVE-2017-0144) was made available by Microsoft in March 2017, giving users nearly two months to install it before WannaCry made global headlines in May. And yet, WannaCry had an unprecedented impact, infecting roughly 200,000 computers across 150 countries and causing up to $4 billion in estimated damages. But EternalBlue didn’t make its biggest impact until six weeks later, when it was used in the NotPetya cyberattacks, which resulted in more than $10 billion in damages, leading some to call it the most devastating cyberattack of all time.
In their immediate aftermath, WannaCry and NotPetya sparked earnest conversations about patching frequency and the need for enterprise IT leaders to push cybersecurity as a more critical issue on the boardroom agenda.
But two years later, it seems this hard-earned lesson has been forgotten by many. Two days after the two-year anniversary of WannaCry, Microsoft patched the BlueKeep vulnerability and even issued a follow-up reminder two weeks later, emphasizing the potential impact of failing to patch the vulnerability. Despite these warnings, companies have been markedly slow to patch BlueKeep, and the release of a commercial exploit to the customers of a U.S.-based security assessment and penetration-testing company last month reignited concerns that it may only be a matter of time before an exploit becomes widely available to cybercriminals.
Why High-Risk Vulnerabilities Go Unpatched
Based on the scenario I’ve laid out, you may be perplexed as to why so companies are failing to patch BlueKeep. However, we must acknowledge the inherent challenges and complexities associated with patch management. Administering security patches is a time- and resource-intensive process that requires rigorous compatibility testing before fixes are distributed enterprisewide. But with hundreds of Common Vulnerabilities and Exposures (CVE) numbers assigned in a typical month, IT security teams are forced to prioritize which vulnerabilities are most critical to their businesses, and test and apply those patches first. A critical vulnerability to one company could just as easily be …
… a vulnerability of moderate severity to another.
Risk-Based Patch Management
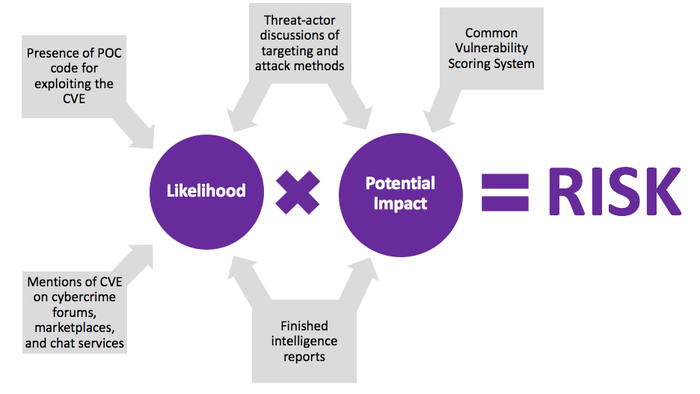
This simplified diagram shows the many inputs required to assess the level of risk posed by a CVE.
For effective patch management, patching should be prioritized based upon which CVEs pose the greatest risk (risk = likelihood x potential impact) to an organization. But without the right resources and tools, determining which CVEs pose the greatest risk to an organization can be a shot in the dark. One of the most common mistakes is to prioritize patching based solely on the Common Vulnerability Scoring System (CVSS). The CVSS quantifies the potential impact of a CVE based on its inherent attributes. However, the likelihood of a vulnerability being weaponized does not factor into the CVSS. Since the majority of CVEs are never weaponized by cybercriminals, this is a critical blind spot that will likely lead to misguided patching decisions.
Two of the strongest indicators of likelihood are whether cybercriminals are talking about a CVE and the existence of proof-of-concept (POC) code indicating adversaries have figured out how to weaponize it. Since some cybercriminals operate within secretive dark-web forums, illicit marketplaces and encrypted chat services, it’s essential for MSSPs team up with partners that collect data from these communities.
Beyond quantitative measures of how many times a CVE has been mentioned and how frequently, the conversations in which a CVE is mentioned can shed light on how it is being weaponized and their intended targeting, adding nuance to a team’s understanding of its likelihood and potential impact.
Since it is crucial that customers can easily access and parse these resources, MSSPs should look for partners that offer searchable, user-friendly CVE dashboards supplemented by finished intelligence reports analyzing notable vulnerabilities in depth, as well as analyst-curated alerts that are tailored to customers’ needs.
Since the majority of cyberattacks exploit known vulnerabilities, solutions that enable more effective patch management have the potential to have a transformative impact. But effective patch management (registration required) requires nuanced decision making based on technical and contextual information about CVEs, so MSSPs should take care in selecting partners that deliver the meaningful insights needed to inform an effective course of action. By doing so, MSSPs can better position themselves within the cybersecurity space and add significant value to their offerings.
As senior director, head of worldwide channels and partnerships at Flashpoint, Ayesha Prakash leverages her extensive experience driving business development and marketing efforts in the IT sector to build Flashpoint’s global channel program. Follow her on Twitter @yoursocialnerd and @FlashpointIntel.
Read more about:
MSPsAbout the Author
You May Also Like


