Cisco Midyear Security Report: 5 Takeaways for PartnersCisco Midyear Security Report: 5 Takeaways for Partners
Deep insights into networks large and small pay off in security advice.
July 20, 2017

Cisco’s 2017 Midyear Cybersecurity Report draws on the company’s broad view into networks – a daily feed of more than 40 billion points of telemetry – as well as insights from security technology partners including Qualys, Radware, Rapid7, RSA and ThreatConnect.
The headline: Attacks leveraging IoT and other connected devices could rise to levels that Cisco calls “destruction of service” and result in the decimation of customers’ backups and the systems required to restore operations and data after an attack. Mobilization of IoT botnets could potentially disrupt the Internet itself.
A sampling of findings that partners will find useful when discussing security with customers include:
1. Ransomware. Now for lazy crooks, too. Cisco says that in 2016, about half of all companies suffered at least one cyber-ransom incident, either a ransomware attack (39 percent) or a ransom denial-of-service (RDoS) attack (17 percent). And, all businesses are at risk: Twenty-nine percent of SMBs reported ransomware compared with 21 percent of organizations with more than 10,000 employees. Customers may not have RDoS on their radars, but the typical ransom demand is 10 to 200 bitcoins, or about $3,600 to $70,000. Don’t pay, and the attackers may take down the target’s networks with traffic volumes typically exceeding 100 Gbps. Demands on the lower end of that bitcoin spectrum may signal a bluff; in the full report, Cisco lays out four signs that the group demanding payment may not have the means to actually launch an attack. Ransomware as a service, where unsophisticated groups buy exploits, is also on the rise. Action: Protection against encryption ransomware is a multi-pronged effort. Deflecting DDoS attacks of any sort demands preparation, including evaluating if the customer needs a DDoS mitigation service.
 2. Email fraud is costly and on the rise: Business email compromises include crooks pretending to be a CEO and conning a CFO into making a wire transfer — one company was taken for $480,000, but insurance refused to cover the loss. According to the Internet Crime Complaint Center, $5.3 billion was stolen due to business email fraud between October 2013 and December 2016. In comparison, ransomware exploits took in $1 billion in 2016. Action: Cisco says combating email fraud usually requires improvements in education and business processes, as opposed to threat defense tools. For example, you might recommend that customers require employees to verify all wire transfers with the requesting employee by phone.
2. Email fraud is costly and on the rise: Business email compromises include crooks pretending to be a CEO and conning a CFO into making a wire transfer — one company was taken for $480,000, but insurance refused to cover the loss. According to the Internet Crime Complaint Center, $5.3 billion was stolen due to business email fraud between October 2013 and December 2016. In comparison, ransomware exploits took in $1 billion in 2016. Action: Cisco says combating email fraud usually requires improvements in education and business processes, as opposed to threat defense tools. For example, you might recommend that customers require employees to verify all wire transfers with the requesting employee by phone.
3. Spam volume has risen since mid-2016. Cisco’s explanation is that adversaries who had relied heavily on exploit kits to deliver ransomware are turning to spam emails, including messages containing macro-laden documents that can defeat many sandboxing technologies, if the attacker can trick a user into opening the file. Threat researchers anticipate that the volume of spam with malicious attachments will continue to rise while the exploit kit landscape remains in flux. Action: Make sure spam filtering technology is in place at the gateway. Better to keep malicious email from …
… ever reaching users’ inboxes than depend on them not clicking a link or opening a document purporting to be from a colleague or trusted source.
4. Convenience and security don’t always mix. Cisco says open authorization (OAuth) risk and poor management of privileged user accounts create security gaps, and malicious hackers have already taken advantage. OAuth refers to that handy app authentication specification that allows us to use our Google or Twitter accounts to authenticate to a third-party service without setting up a new username and password. In fact, Google just announced that it will warn users when unverified apps request access to their accounts. Action: Google provided steps to compensate for OAuth’s weaknesses, including turning on two-step verification for your organization and using security keys, publishing a DMARC policy for the organization and enforcing rules for S/MIME encryption.
5. Patching vigilance pays off. Cisco says timely patching of Flash, which is riddled with security flaws, has helped slow the growth and innovation in the exploit kit market. However, when one door closes, attackers look for another, and researchers worry that they’ll find openings in IoT devices — specifically medical devices that were not designed with security in mind, are often running old and unpatched software and are rarely monitored. Action: Customers that run unsupported versions of Windows on desktops or servers are at risk since Microsoft isn’t issuing patches, except for extraordinary circumstances, such as May’s remote code execution flaw. In the Cisco report, TrapX researchers discuss the exploitation of an oncology system with known Windows XP vulnerabilities. Cisco also recommends keeping older signatures active, surrounding IoT devices with IPS defenses and closely monitoring network traffic. Our IoT security report explains the three must-have pillars of a profitable IoT program and the security considerations intrinsic to each element. Patching software and firmware wherever possible is high on the list.
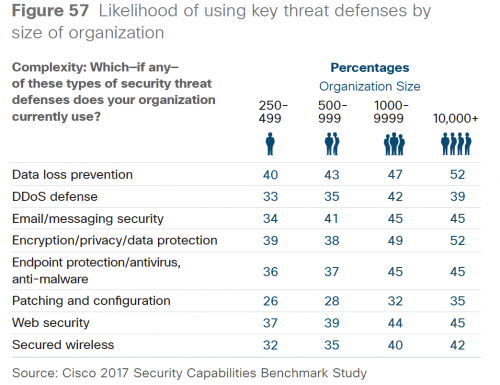
The Cisco report also discusses how security preparations vary by customer size. For example, only 34 percent of SMBs reporting using email security compared with 45 percent of large organizations. And, 40 percent of SMBs use data loss prevention compared with 52 percent of large organizations.
Cisco points out that service providers, including CSPs, MSPs and MSSPs, have much to lose if they themselves are successfully attacked. More than half, 57 percent, of the service providers responding to the survey said they had dealt with public scrutiny due to a data breach, 34 percent reported revenue losses due to attacks in the past year, and about 30 percent report losing customers or business opportunities due to attacks.
Finally, no surprise, the report says security expertise is scarce, and that is an opportunity for partners. Among U.S. SMB respondents, 54 percent outsource monitoring; 44 percent of larger enterprises say the same. Just 14 percent and 15 percent, respectively, don’t use an outside provider for any of the six security functions discussed.
Dave Gronner, senior manager, security go-to-market within the Cisco global partner organization, says that the skills shortage means channel partners need to offer managed services to help customers assess their threat profiles and develop strategies to minimize risk. Gronner says these services should be tailored to a customer’s vertical and company size and include a plan to protect IoT devices, such as the DVRs that were part of the massive Mirai DDoS attacks that brought down sites including Twitter, the Guardian, Netflix, Reddit and CNN in December.
Download the full report here for more insights.
Security is also a key focus at Channel Partners Evolution, held in Austin Sept. 25-28. Attend our first-ever half-day ransomware preconference, learn what evil lurks in the dark web and why it matters to customers, and get in-depth info on using isolated backups to restore lost data. Register now — our room block is selling out fast!
Read more about:
AgentsAbout the Author
You May Also Like


