4 Takeaways from Verizon's Data Breach Investigations Report: Wising up to Phishing?4 Takeaways from Verizon's Data Breach Investigations Report: Wising up to Phishing?
Employees are getting smart about phishing, but their bosses? Not so much.

“Why don’t we skip all the hard hacking and just, you know, ask for the money?”
That simple mindset drives cybercriminals to con executives into unwittingly handing over precious data, according to the 2019 Verizon Data Breach Investigations Report (DBIR).
The likelihood of senior executives succumbing to social breaches was nine times more likely than in previous years, according to the study. Many of these breaches could have been prevented with rudimentary security protocol, according to Gabe Bassett, the senior information security data scientist on the Verizon Security Research team.
Hi y’all. Today I get to share the 2019 @VZDBIR with you: https://t.co/JwybL24WpT It’s been 6mo and 73 contributors in the making. If you haven’t heard of it, it’s a data driven report on the incidents and breaches from the last year. We hope it helps you improve your defenses!
— Gabe The Engineer (@gdbassett) May 8, 2019
Verizon unveiled results from its 2019 Data Breach Investigations Report Wednesday. The data shows the demographics of both attackers and victims shifting. Below are four interesting findings.

Verizon’s Gabe Bassett
Phishing for Execs
The C-suite saw a target on its back in the last year, getting particularly hammered in the professional services industry, where they accounted for 20 percent of the compromises.
Bassett said social pretexting – better known as phishing – is a chief strategy that turns your boss into a sucker. Most cases of phishing saw the threat actor exploit a person using a link or an attachment. The attachments are typically macro-enabled Microsoft Office documents or Windows executables.
Businesses should have policies in place to filter out a significant portion of these attacks.
Source: Verizon Data Breach Investigations Report
“The reality is, no one’s getting their software updates by email,” Bassett said. “So block Windows executables at the mail gateway. Block macro-enabled Office documents at the mail gateway. Block links at the mail gateway and let people go in and say, ‘Yes, this is something I was expecting.'”
But there’s great news on the phishing front: Employees are catching on. Click rates in phishing exercises dipped below 3% this year, according to the study. Thirty-two percent of breaches involved phishing last year, according to the report, so businesses may be rising to the challenge of one of the most popular threat actions. Your move, bad guys.
A Shift in Perpetrators
Outsider threats remain most prevalent, but we’ve seen a slow but consistent changing of the guard over the last few years. Outsiders perpetrated 75% of breaches in 2017, with inside actors involved in 25% of them. The ratio turned to 73-28 in 2018 and sits at 69-34 in 2019. That doesn’t mean the insiders have malicious intentions, but as we discussed in the previous paragraph, even the most well-intentioned employees can be complicit in a breach if they lack the proper education and protocal.
SMBs Drop
Small and medium-size businesses accounted for a smaller percentage of breaches than in previous years. Bassett and the Verizon team didn’t discover any clear drivers, but the results are quite suggestive.
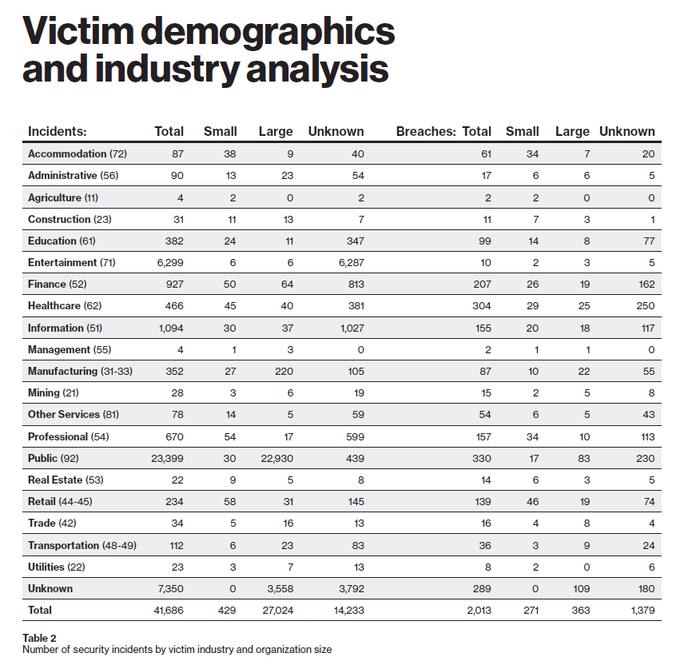
Forty-three percent of the breached companies in the latest report are categorized as SMBs. That’s still a staggering number, but it represents a decrease of sorts. We wrote in 2017 that the number was 61%. The percentage dropped to 58 in 2018.
Source: 2019 Verizon Data Breach Investigations Report
One of the steps SMBs can do to improve their data protection is …… to ensure that they have a solid process in place for validating money transfer, Bassett said. For the businesses that are behind the curve on security, there’s value in at least trying. Start by doing enough to negate the “zero-marginal cost attack,” which is a cybercriminal’s dream. Simply put, the bad guys want a target that requires minimal resources and time to crack.
“You don’t have to be perfect,” Bassett said. “Try to at least get above the bar so those automated attacks don’t work.”
Another area of table stakes is two-factor authentication, according to Bassett. Apparently channel experts haven’t drilled the importance of that into everyone’s heads yet.
“Four years ago was the time to get on that two-factor authentication project,” he said. “Now it’s behind the curve, and its time to play catch-up.”
We examined the outsider-insider disparity and the irregularity of healthcare in last year’s DBIR write-up.
Read more about:
AgentsAbout the Author
You May Also Like


