Arbor Survey Shows DDoS Attacks on the Rise
Partners have options to protect customers, but prior planning is key.
January 26, 2016

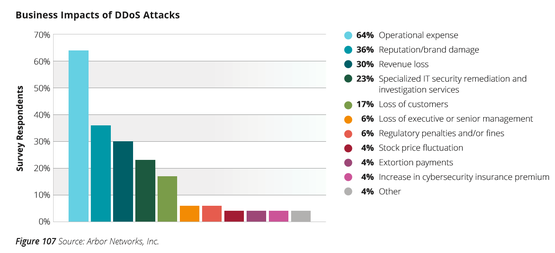
 Distributed denial-of-service attacks are getting bigger, badder and more widespread, says Arbor Networks’ new Worldwide Infrastructure Security Report, which covers a range of topics, from detection of and incident response to DDoS attacks to staffing, best practices and business impacts.
Distributed denial-of-service attacks are getting bigger, badder and more widespread, says Arbor Networks’ new Worldwide Infrastructure Security Report, which covers a range of topics, from detection of and incident response to DDoS attacks to staffing, best practices and business impacts.
Nearly half (48 percent) of the 354 respondents hail from enterprise, government or educational organizations, with service providers making up the remaining 52 percent.
For the channel, Arbor says the complexity of DDoS, and security overall, is increasing demand for managed security and incident-response services as well as new products.{ad}
 “Respondents are definitely investing in technologies to speed their incident response times,” says Gary Sockrider, principle security technologist at Arbor Networks. Worldwide. “It’s a top concern.”
“Respondents are definitely investing in technologies to speed their incident response times,” says Gary Sockrider, principle security technologist at Arbor Networks. Worldwide. “It’s a top concern.”
Channel Partners spoke with Sockrider about the outlook for DDoS attacks, which are growing at an alarming rate. The largest verified attack for 2015 was 500 Gbps. Eleven years ago, when Arbor began the survey, it was 8 Gbps.
“This year, over half of data-center operators told us they experienced DDoS attacks that exhausted their entire Internet bandwidth for the data center, up from one-third last year,” says Sockrider.
And while large-volume assaults make headlines, he’s seeing more application-layer and state-exhaustion attacks that can plow through customers’ defenses. Fifty-six percent of respondents reported multi-vector attacks targeting infrastructure, applications and services simultaneously, while over half of respondents saw failures in firewalls, load balancers and other common security gear as a result of DDoS attacks.
“That number has been going up year on year,” he says. “Any device that maintains a state table is …
{vpipagebreak}
… vulnerable.”
Arbor also saw a huge increase in attacks on data centers, as malicious actors follow workloads into the cloud.
As to which applications are being targeted, as expected, the top responses are Web services — HTTP, HTTPS and DNS. For the first time, however, DNS was the most-reported target. And, DDoS attacks over IPv6 are up from 2 percent last year to 9 percent this year, a steep increase.
“DNS is both a target and a tool,” says Sockrider, and customers using DNSSEC may not gain a safety advantage, depending on how it’s implemented.
“Simply locking down a DNS server so that it doesn’t respond to requests that come from outside your network would cut down on a huge amount of this stuff,” says Sockrider. “That one simple configuration change could make a huge impact.”
However, this is far from common practice.
“Last time I checked, there are something like 25 million vulnerable DNS servers on the public Internet,” he says.
DDoS Trends
When talking to customers, a few findings stand out as motivators to invest in DDoS mitigation technology and services. For one, this year, the top motivation for attackers was not hacktivism or vandalism but criminals demonstrating attack capabilities. At No. 3 is criminal extortion attempts — DDoS for Bitcoin is the new ransomware.
“This is the first time in three, maybe four years that the top motivation wasn’t ideological hacktivism,” says Sockrider. “The other [motivation] that deserves a callout is DDoS use as a distraction or diversion for either infiltration of malware or exfiltration of data.” The percentage naming that as a driver is moving up, reaching 26 percent.
Frequency is up as well, with 28 percent of respondents seeing more than 10 attacks per month. That’s expected in the service-provider space, but for enterprises, it’s a real challenge.
“In data centers, 9 percent saw more than 50 attacks per month,” says Sockrider. “No data-center operators said the same last year. That’s pretty darn significant.”
Most enterprise respondents (75 percent) have developed formal incident-response plans and dedicated at least some …
{vpipagebreak}
… resources to respond to DDoS attacks, up from approximately two-thirds last year. However, there are gaps. In particular, the skills shortage has led to an increase in the use of managed services and outsourced support. Half of enterprises have engaged solutions providers or MSSPs for incident response.
Even SMBs may be targets, and partners serving small companies have new options to protect them. Over the past few years, Arbor, like most DDoS protection vendors, has broadened its portfolio, adding cloud-based as-a-service and virtual versions of its offerings, and Sockrider says the company is seeing strong growth.
“As of this year we have virtualized all the appliances, we now offer a cloud solution, and of course we still offer the appliance model,” he says. Between the service and virtual and hardware appliances, the company can cover SMB, enterprise and service-provider customers.
“We’re definitely seeing a strong ramp in the service model,” he says. “That, and the virtual appliances, are really driving our growth in the enterprise space and the channel. It’s a product that’s accessible to a much larger cross-section of organizations.”
Arbor Networks is the security division of NetScout. Its partner program offers technical training and support, among other benefits, and it recently launched a collaboration with Cisco to host a virtual version of its DDoS mitigation appliance on a blade in Cisco’s ISR 9000 routers. Rather than routing traffic across the WAN to a scrubbing center, you can help customers mitigate close to the egress point of an attack.
“What you don’t want to do is back-haul a DDoS attack across your backbone,” says Sockrider.
Arbor also uses OpenFlow to communicate between the virtual appliance on the blade and the router itself; if an attack is detected, the ISR 9000 can use an ACL to block a large volume of suspect traffic.
“It allows you to scale in a way that you just couldn’t do with an appliance alone,” he says.
Follow executive editor @LornaGarey on Twitter.
Read more about:
AgentsAbout the Author
You May Also Like


