'Critical' Palo Alto Vulnerability Gets a Fix: Attacks Confirmed
A "limited number of attacks" have occurred using the vulnerability, Palo Alto shared.

Palo Alto Networks is urgently calling for customers to update three of their firewall operating systems to patch a software vulnerability.
News surfaced late last week of a command injection vulnerability in three of Palo Alto's firewall operating systems. The company on Thursday confirmed the weakness, named CVE-2024-3400, and has been communicating with with researchers, partners and customers. The cybersecurity provider on Sunday announced hotfixes for the three affected operating systems.
Threat intelligence and incident suppression services provider Volexity first discovered the vulnerability. Palo Alto rates the severity of the vulnerability at 10 — its most critical level.
What Is the Palo Alto Vulnerability?
Palo Alto states that the problem occurs in PAN-OS 10.2, PAN-OS 11.0 and PAN-OS 11.1 firewalls that are configured either on Palo Alto's GlobalProtect gateway or GlobalProtect portal and have enabled device telemetry.
Fortunately, the vulnerability did not exist on Palo Alto's Cloud NGFW (next-generation firewall), its Panorama management devices or its Prisma Access secure access service edge (SASE).
According to Palo Alto's Unit 42 incident response team, the command injection vulnerability in the software lets unauthorized users "execute arbitrary code with root privileges on the firewall."
Palo Alto also created a threat ID for customers to add to their GlobalProtect interface. Customers that don't subscribe to threat prevention mitigation from Palo Alto Networks were encouraged to temporarily disable device telemetry until they have upgraded their PAN-OS.
Read more information in Palo Alto's security advisory blog.
Have There Been Attacks?
Palo Alto acknowledged that it is aware of "a limited number of attacks" leveraging the vulnerability.
According to Volexity, a threat actor first successfully exploited the vulnerability on March 26. Volexity said it observed the threat actor, which it calls UTA0218, "deploying malicious payloads" using the firewall vulnerability on April 10. Volexity said it alerted Palo Alto the problem on April 10.
A second compromise occurred on April 11, according to Volexity.
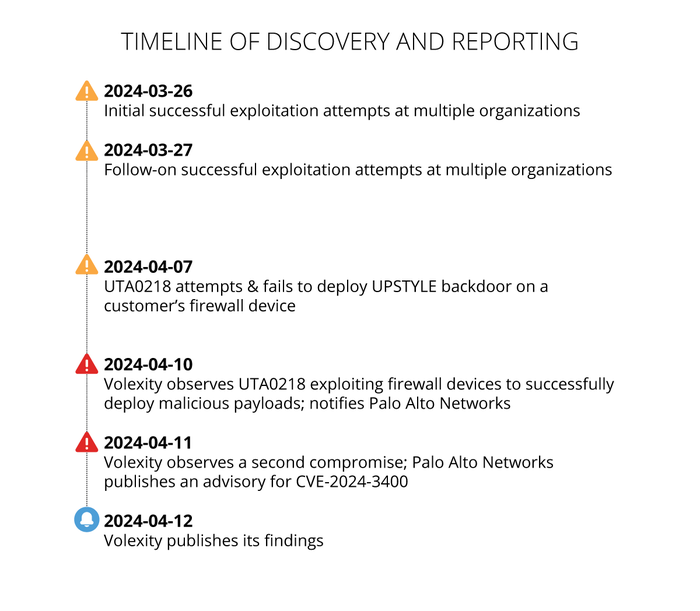
Source: Volexity
Volexity writes that the threat actor in one case accessed a "highly privileged service account" and made its way into the internal network to target the Active Directory database and other key data and logs.
Volexity added that it did not observe any malware deployment or "additional methods of persistence."
"The stolen data did allow the attacker to effectively compromise credentials for all domain accounts," the company wrote in a blog. "Further, the attacker gained access and could potentially use valid credentials or cookies taken from browser data for specific user workstations accessed."
About the Author
You May Also Like


