Nearly 100% of Applications Vulnerable, Says Trustwave Report
Cybercrime as a business model pays, but partners can help customers protect data.
April 19, 2016

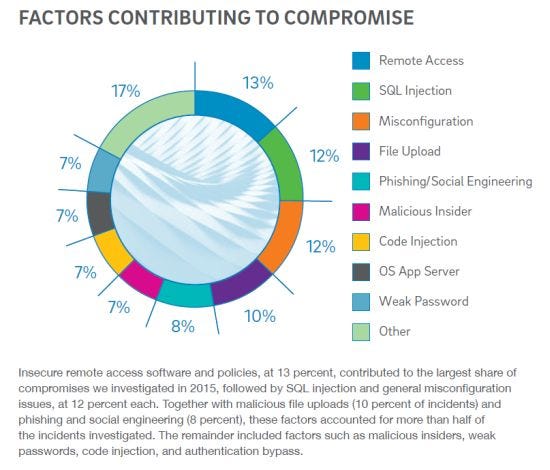
 Channel-focused security firm Trustwave released Tuesday its 2016 Trustwave Global Security Report based on data from breach investigations as well as logged security and compliance events. The insights should help partners drive home the need for proactive security, especially for those serving the retail vertical — it was the most compromised industry, making up 23 percent of investigations, followed by hospitality and food and beverage.
Channel-focused security firm Trustwave released Tuesday its 2016 Trustwave Global Security Report based on data from breach investigations as well as logged security and compliance events. The insights should help partners drive home the need for proactive security, especially for those serving the retail vertical — it was the most compromised industry, making up 23 percent of investigations, followed by hospitality and food and beverage.
Not surprisingly, 38 percent of investigations were around e-commerce breaches. While successful attacks on point-of-sale (POS) systems are down, they’re still an area of concern. In 60 percent of cases, attackers were after payment-card data. And, customers are unlikely to spot breaches themselves. Most, 59 percent, were spotted by a third party, and not quickly: A median of 168 days elapsed from intrusion to containment.
 {ad}
{ad}
 No company is safe, however, because cybercrime is a lucrative and well-organized business. Trustwave previously demonstrated how attackers launching a malware infection campaign could earn $84,100 from a $5,900 investment in just 30 days. In some cases, they’re operating on the cloud pay-as-you-go model so popular with customers, subscribing to a service that delivers access to a steady stream of new exploits.
No company is safe, however, because cybercrime is a lucrative and well-organized business. Trustwave previously demonstrated how attackers launching a malware infection campaign could earn $84,100 from a $5,900 investment in just 30 days. In some cases, they’re operating on the cloud pay-as-you-go model so popular with customers, subscribing to a service that delivers access to a steady stream of new exploits.
Michael Petitti, SVP of Global Alliances for Trustwave, said the company hopes the information in the new report will enable its partners to deliver solutions that protect businesses in all industries from the latest threats. And in fact, besides data points that demonstrate the need for security, the 90-page report has extensive recommendations of security measures that Trustwave investigators recommend to mitigate the risk of data compromise. For example, the firm recommends …
{vpipagebreak}
… common-sense practices like limiting Internet access for and segmenting systems connected to a payment processing environment, auditing firewalls for accessible ports and services and avoiding use of generic or default account names. It also digs deeper into protections applicable to customers subject to the Payment Card Industry Data Security Standard.
Don’t Like Spam
An interesting insight is the success the industry has had in cutting down on junk email. In 2015, spam represented 54 percent of total inbound email processed by Trustwave’s Secure Email Gateway Cloud service. Compare that with 2010, when 85 percent of email was spam.
The company credits a combination of a general lack of profitability and a growing fear of prosecution on the part of large botnet operators for the decline.
Still, spam is a big problem. Messages carrying malicious payloads, either as attached files or as links to malware, remained relatively constant, accounting for 5 percent of total spam volume in 2015, down slightly from 6 percent the previous year. Phishing over email is a prime way ransomware is introduced, so partners shouldn’t see reduced volumes as a reason to lessen spam filters and education.
The report suggests ways to help customers limit risk, including deploying an email security gateway that includes anti-spam, anti-malware, and flexible policy-based content filtering capabilities. As for policies, consider quarantining or flagging all executable files and ensuring that macro protection is enabled in Office. Partners will also find sections on data compromise incidents, vulnerabilities and exploits, attacks on web platforms, threats delivered through the Web and other topics.
Follow editor-in-chief @LornaGarey on Twitter.
Read more about:
AgentsAbout the Author
You May Also Like


