AWS Security Best Practices: A Baker's Dozen for Success in the CloudAWS Security Best Practices: A Baker's Dozen for Success in the Cloud
From implementing the principle of least privilege to cloud workload protection, following these tips makes for a more secure cloud infrastructure.
May 16, 2022

By Paul Ardoin

Paul Ardoin
After decades of working in traditional data centers that could get as hot as a busy kitchen in the summer, network administrators got a major update: the cloud. Cloud platforms such as Amazon Web Services (AWS) enable organizations to mix their services and applications into a powerful computing infrastructure. After tasting the delicious results, organizations can be quick to add cloud infrastructure, expanding their menu of services and applications.
However, cloud security is often an overlooked ingredient, folded in just before applications and services are live – which can lead to hard-to-swallow data breaches and security incidents. To defend against the latest cyberthreats, organizations must bake security into their AWS deployments from the start.
This recipe for AWS security best practices provides the latest guidance to implement strong AWS security, establishing a consistent security posture in your AWS environment.
4 Ways to Spoil the AWS Security Broth
In any successful kitchen, cooks must make sure their sauces don’t separate, their souffles don’t fall and their steaks don’t burn. Challenges must be overcome with knowledge, care and the right tools. Likewise, many organizations struggle with the challenges of implementing strong cloud security – these four in particular:
Shared Responsibility Model: Like a chef who must know the flow of the kitchen, organizations must understand their cloud service provider’s shared responsibility model – which security responsibilities belong to the CSP or the customer – and know how to fulfill their responsibilities. Otherwise, they can unintentionally create security gaps.
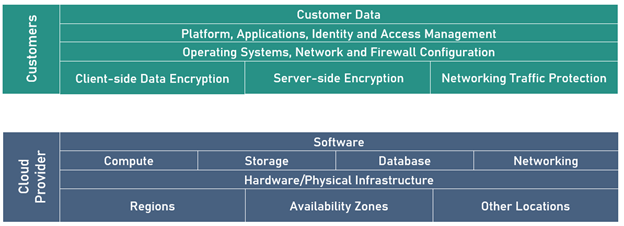
Figure 1. A sample shared responsibility model. Courtesy: Check Point Software Technologies
Maintaining Visibility: In a well-run kitchen, you won’t find the accounting staff cooking pasta on a hot plate during the dinner rush. So how can an organization be successful when employees set up cloud deployments without IT’s knowledge? “Shadow IT” makes it difficult to determine what IT needs to monitor. Similarly, chefs must know which ingredients are arriving every day. Yet some companies provision and decommission cloud assets rapidly, complicating their management.
Meeting Compliance Requirements: Restaurants must follow safety rules for food storage, temperature controls and more. Likewise, most companies are subject to different regulations regarding sensitive information and unauthorized access. In the cloud, a company does not have direct control over the underlying infrastructure, so achieving and demonstrating compliance is more complex.
Enforcing Consistent Security Policies: If a restaurant opens other locations, customers expect the same quality, atmosphere and service, even though they are in different buildings using different equipment. According to the Cybersecurity Insiders 2022 Cloud Security Report, most organizations have at least two public clouds, each with their own tools and configurations. Enforcing consistent security policies across all environments can be challenging, especially configuring and maintaining cybersecurity settings for each environment.
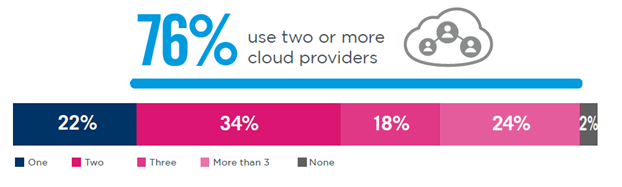
Courtesy: Cybersecurity Insiders 2022 Cloud Security Report
13 Ingredients for Effective AWS Security
Achieving strong cybersecurity in the cloud can seem daunting, but by following this AWS security best-practices checklist, it’s possible to …
… enhance the security of an AWS deployment.
Identify Security Requirements
Define and categorize assets in AWS: Chefs can’t create a great menu without knowing what’s in their kitchen. Likewise, you can’t secure systems you don’t know exist. The first step to improve AWS security is to identify the assets that you have and separate them into categories.
Create classifications for data and applications: Next, assign each asset (or category) a security classification based upon the data’s sensitivity and importance. These classifications should map to the asset’s required level of protection and controls.
Deploy Solutions Designed to Solve Cloud Security Challenges
Much like a formal dining establishment needs a different approach to business than a fast-food place, so, too, does cloud-based infrastructure require different security approaches and tools than traditional environments:
Manage cloud access: Limit access to cloud-based infrastructure, as users can access cloud-based resources directly without sending traffic through an existing network perimeter (and its security stack).
Use cloud-native security solutions: Security solutions designed for traditional data centers have limited functionality in the cloud. Cloud-native solutions place security functionality next to the appropriate assets and provide optimal performance.
Protect all your connections and segment everything: On-premises security often focuses on a single perimeter: the network connection with the outside world. In contrast, cloud security controls multiple ingress and egress points: one or more for each cloud-native service, as well as north-south (client to server) and east-west (server to server) traffic. Effectively separating and segmenting cloud workloads helps contain the impact of a breach.
Maintain a Consistent Security Posture
In a restaurant kitchen, if equipment doesn’t work or employee schedules are mismanaged, disaster – and angry customers – can result. In the same way, settings and configurations in AWS must be correct. Tools can ensure a consistent cloud security posture:
Manage AWS accounts and IAM users, groups and roles: Implementing the principle of least privilege — only the access and permissions needed — is an essential identity and access management (IAM) function.
Manage access to Amazon EC2: With unauthorized access to EC2 instances, attackers could access sensitive data or introduce malware. Controlling access to EC2 based upon the principle of least privilege is necessary to minimize risk.
Protect AWS Workloads
When an innovative cooking device is introduced, a kitchen must understand how that innovation fits in, so that it enhances rather than disrupts the restaurant’s workflow. Similarly, innovations such as serverless and containerized deployments must enhance the business, so they require purpose-built security solutions:
Protect for serverless and containers: Microservice workloads require unique security solutions. It’s essential to deploy cloud workload protection, including observability, least privilege enforcement and threat prevention functionality.
Implement Proactive Cloud Security
Successful restaurants take many steps to keep pests out, maintain equipment and train staff – they don’t wait until a dinner service goes haywire. Yet many organizations only respond once a cyberthreat is active, which puts the organization at risk. A more proactive security strategy prevents threats:
Subscribe to threat intelligence feeds: Threat intelligence provides valuable information and indicators of compromise.
Perform threat hunting in AWS: Proactive threat hunts, where cybersecurity analysts look for signs of potential incursions into their network, enables an organization to identify and remediate threats before attackers can gain access.
Define incident response policies and procedures: Good restaurants won’t serve meals that use out-of-date ingredients. So why are so many cybersecurity procedures obsolete? Updating and adapting policies to address cloud-based deployments is essential to effective remediation.
Ensure Regulatory Compliance
If kitchens don’t follow health and food safety guidelines, their customers could get sick – and they could face heavy fines. Most organizations are subject to regulations to protect customer data. To help ensure continuous compliance with regulations in the cloud:
Ensure visibility of controls: Data protection regulations specify that organizations implement an array of security controls to protect sensitive data, defending particular attack vectors and providing continuous visibility.
Continuously verify compliance: Deployments must meet the needs of applicable regulations and close security gaps.
Much like different restaurants have different needs in their kitchens, different infrastructures require different strategies and tools. Adapting security approaches to AWS makes organizations more dynamic and agile.
Paul Ardoin manages cloud alliance marketing at Check Point Software Technologies. He has spent most of his more than 25-year career in marketing and public relations with security and networking companies. His articles on computer security have been published in California Computer News and European Communications. He also has written mystery novels that feature cybersecurity issues. You may follow him on LinkedIn or @CheckPointSW on Twitter.
You May Also Like
