What MSPs Can Learn from WannaCry RansomwareWhat MSPs Can Learn from WannaCry Ransomware
WannaCry was so successful because it hit many computers that were connected only to an internal network--not the internet—and thus were erroneously assumed to be safe from ransomware attacks. This should remind MSPs that overlooked or obscure system vulnerabilities can quickly become virulent attack vectors.
July 28, 2017

Sponsored by Webroot
It’s highly unlikely that any criminals driving the current ransomware epidemic are familiar with old-time baseball player Wee Willie Keeler, or his famous advice to “hit ‘em where they ain’t,” but the recent success of the WannaCry ransomware cryptoworm suggests some crooks are unwittingly embracing that batting tip. More to the point, it should remind MSPs that overlooked or obscure system vulnerabilities can quickly become virulent attack vectors.
Specifically, WannaCry’s perpetrators did not rely on the traditional (and thus more easily anticipated and blocked) tactic of phishing to spread their infection; instead they “hit ‘em where they ain’t” by employing a network worm approach that exploited file sharing vulnerabilities in the Server Message Block (SMB) protocol in Windows.
The result was the most successful ransomware ever released. The WannaCry attack began on May 12, 2017, and in less than 30 minutes almost a quarter million machines had been infected (see Figure 1):
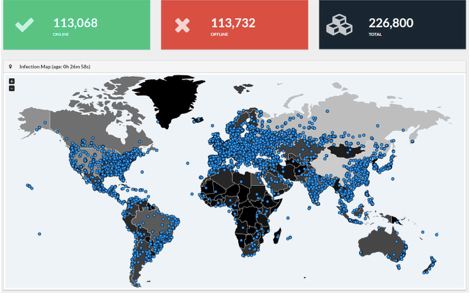
Figure 1: WannaCry ransomware spread at record-breaking pace.
Within one day, it was reported to have infected more than 2 million computers in over 150 countries. Below is the image that WannaCry victims were confronted by on their screens. (Note that the perpetrators went to the trouble of also changing the user’s desktop background.)
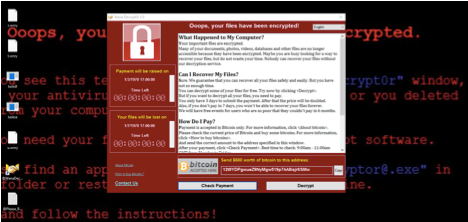
Figure 2: WannaCry victims encountered typical demand for Bitcoin payment.
It’s likely that some of WannaCry’s victims were particularly startled to see this infection, as it’s quite possible that no users had touched the infected machine recently. Because WannaCry victims are infected from other computers on the network internally, or from outside systems that were scanning telnet for SMB running on the machine, any protections against previous ransomware strains that are propagated through the internet were ineffectual.
To its credit, Microsoft patched this vulnerability dating back to fall of 2016. Microsoft was already warning users to disable SMB1, but as these infection rates show, many people did not install the patch.
WannaCry was extremely prolific because it hit so many machines that weren’t considered vulnerable to previous ransomware strains; these computers were only connected to an internal network—but not the internet—and thus were erroneously assumed to be safe from ransomware attacks.
The consequences of that erroneous assumption were devastating:
61 NHS organizations in Great Britain were disrupted, forcing them to turn away patients as their unpatched systems were infected, thus rendering key machines (MRI, X-ray, lasers, blood analyzers, etc.) inoperable.
Some Renault automobile factories had to halt production.
Telecoms, along with power and gas utility companies, in Spain were hit, with employees being told to just “turn off the computers.”
Thanks to the efforts of U.K. researcher MalwareTech, a “kill switch” hard-coded within WannaCry was discovered, effectively stopping the ransomware in its tracks because there were specific domains in the code that would prevent it from executing if it connected to those domains. Webroot quickly ensured those kill switch domains were categorized and allowed, but obviously this prevention measure didn’t last long, as many variants are now constantly changing the kill switch addresses or just removing them altogether.
The most effective protection measure is to immediately apply the patches that Microsoft has released for all currently supported Windows versions. Within four days of the initial outbreak, security experts said, most organizations had applied those updates and new infections had slowed to a trickle.
Key Takeaway: Secure Every Opening, However Obscure
MSPs know well that keeping up with the seemingly endless stream of patches and updates can be challenging and time-consuming, but the WannaCry saga clearly illustrates the enormous costs that you and your clients could suffer if patches are overlooked. Security vulnerabilities can arise from many sources, both obvious and obscure, and your best defense is to block them all.
Guest blogs such as this one are published monthly and are part of MSPmentor’s annual platinum sponsorship.
You May Also Like
