Attackers Have Office 365, G-Suite in Their SightsAttackers Have Office 365, G-Suite in Their Sights
How they get in, what they do once they’re inside, and what you can do to prevent attacks in the first place.
November 19, 2019

Sponsored by AT&T Cybersecurity
Oh, the places we go . . . with apps in the cloud.
A comprehensive six-month study released by Proofpoint reports that (oh, to our surprise) attackers are “leveraging legacy protocols and credential dumps to increase the speed and effectiveness of brute force account compromises at scale.”
Threat actors design threats aiming at platforms or services that will provide the greatest ROI for them. This means targeting attacks on systems that have the greatest number of users. As such, most of today’s attacks are targeted at Microsoft Office 365 (the world’s most widely used productivity suite) and G-Suite.
What Happens When They Get In?
According to the report, once hackers get into a “trusted” account, they launch an internal phishing attack or a business email compromise (BEC) attack, with the ultimate goal of extending their reach into the organization so they can do things such as steal money or information. (Financial gain is a big motive in these types of attacks.)
Here’s a rough overview of how it works:
Attackers compromise a cloud account via a phishing campaign or by stealing an employee’s credentials.
Once hackers have control of the account, they move laterally within the SaaS environment to compromise other user account (we’re talking multiple)–which is easier to do since other employees trust the account they’re getting emails or attachments from.
From there, attackers can do many things, including launching man in the middle (MITM) attacks or setting “mail delegation” (i.e., when you grant access to your account to another person).
The ultimate goal, typically, is to get money or information.
If you want to know more about BEC attacks, check out Trustwave’s blogs which does a great job of summarizing many of the approaches scammers take, including the use of business domains in emails that look similar to the email of an executive at a targeted company.
Staying on Top of the Cloud and Ahead of the Bad Guys
Among the “layered security” needed to protect your cloud assets, the AT&T USM Anywhere Office 365 App can be used to monitor cloud activity, including excessive failed logins, such as the ones mentioned in the Proofpoint report. (Note: it monitors other potentially malicious activity, including file activity, and it brings in the context of your on-prem environment, as well.)
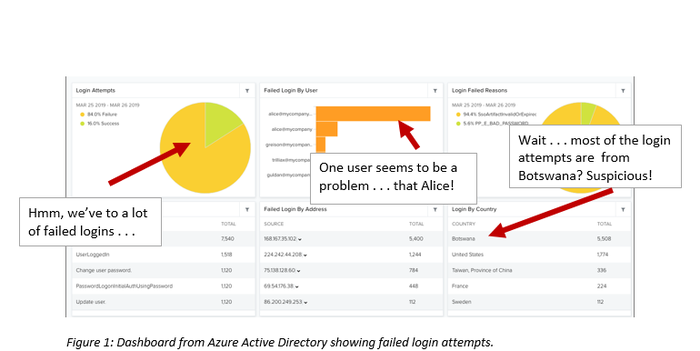
The screen shot in figure 1, for example, shows a dashboard for Microsoft Azure Directory with information on login activity–with quite a few failed login attempts.
One particular user, “Alice,” is apparently the main culprit (or someone trying to pose as Alice). You can also see the login by country of origin. In this case, we’re seeing a spike in logins originating from Botswana. This might be worth looking into, considering that “Alice” works out of a U.S. office.
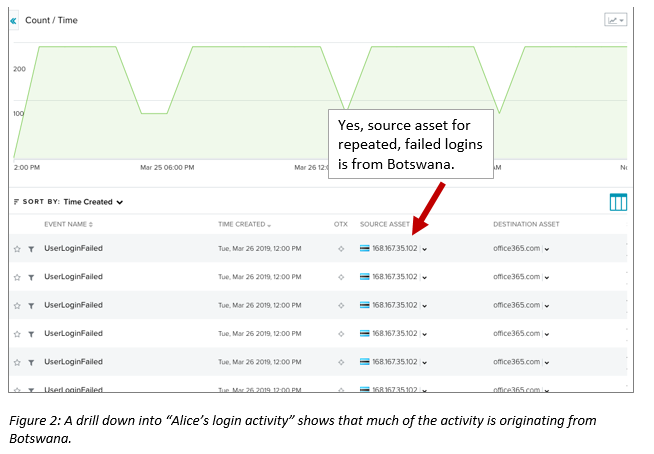
We can drill down to see even more detail on Alice’s login activity, noticing that the source asset for the login is definitely coming from Botswana. This doesn’t look good.
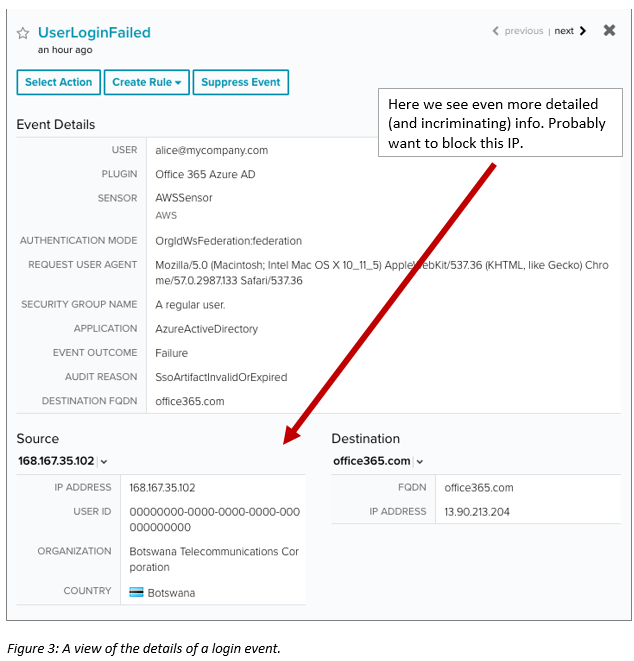
Drilling down deeper, we see even more information (Figure 3). Unless Alice has made a recent trip to Africa, and is now trying to work while on vacation, this is definitely an indication that something is not right–probably a brute force authentication attack. From here, you have multiple options, such as going in and blocking that particular IP address.
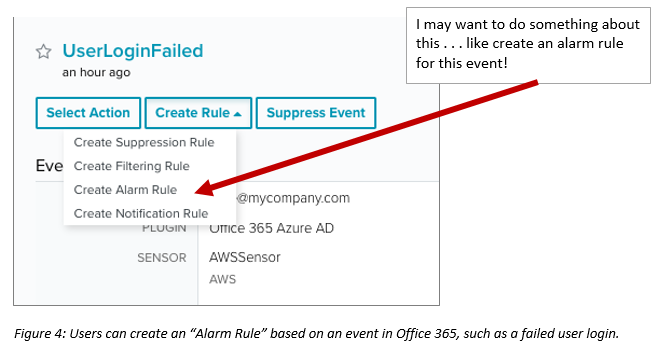
Also, within AlienVault USM Anywhere, you can also do such things as creating an “alarm rule” for the future.
Now, Let’s Make This Easier
The AT&T Security team regularly updates threat intelligence and writes correlation rules to detect threats in the cloud, including in your Office 365 SaaS environment. (Caveat: It’s impossible to write correlation rules for every threat in the universe, but we have created hundreds, and are continuously updating those rules as well as adding more daily.)
For Office 365, for example, we’ve created a correlation rule for “Delivery & Attack | Brute Force Authentication | IMAP”–that is, using automation to repeatedly test a username/password field by using random inputs such as dictionary terms or known username/password lists.
The screen shot in figure 5 shows a summary of alarms triggered for “successful authentication after brute force.” This also includes all the associated events (a number of failed user logins), priority of the alarms, username, source IP and more.
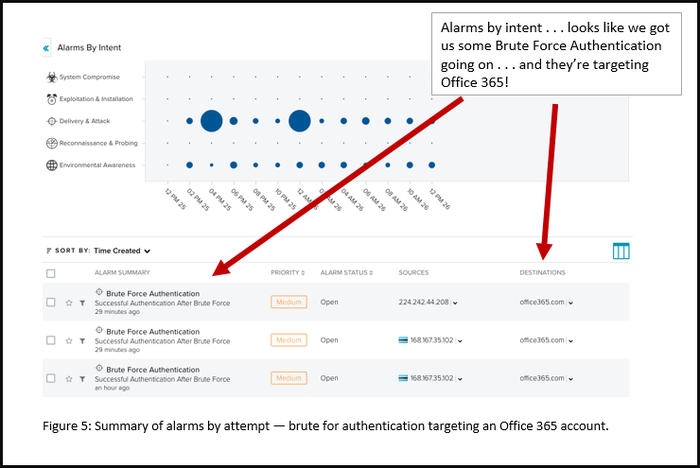
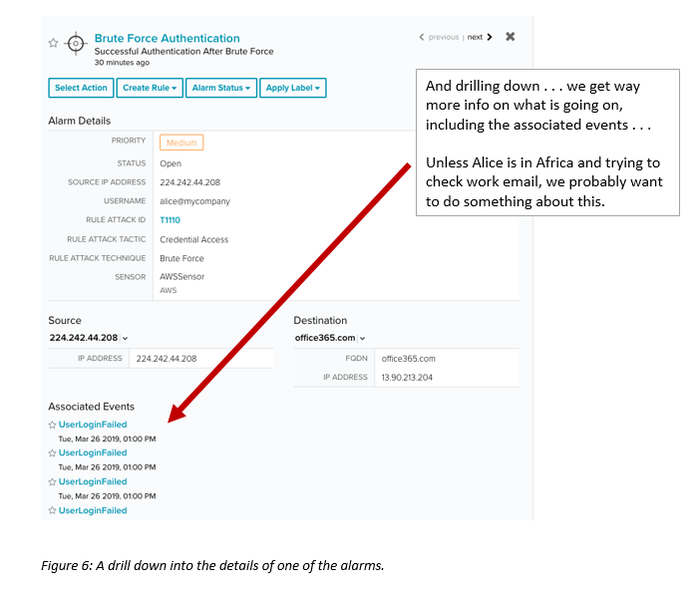
Users can drill down to get even more information, including associated events (such as number of user login attempts and failures). In addition, the alarm shows the MITRE ATT&CK “rule attack tactic” (credential access) and “rule attack technique” (brute force). This is good for those of you who are using the ATT&CK framework as a best practice in your threat detection and response strategy. (AT&T Security has mapped all its correlation rules to the ATT&CK framework. You can read more about the MITRE ATT&CK dashboard here.)
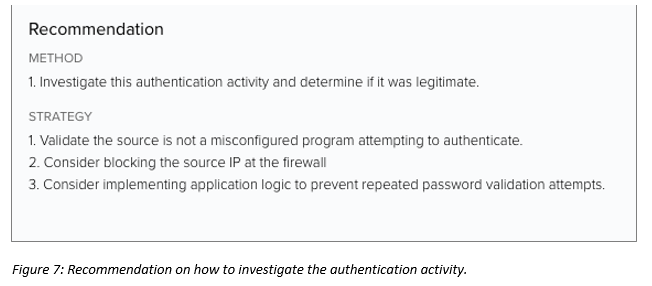
Alarms also include recommendations on what to do next and how to do it (figure 7).
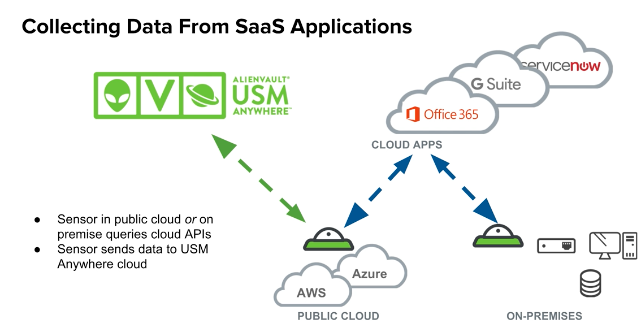
One final consideration in terms of protecting cloud accounts: They don’t live in a vacuum. If you’re like the bulk of organizations out there, you’re probably using multiple cloud services providers (IaaS, PaaS and Saas) combined with your on-prem network. Gaining visibility into all these environments—and the threats to them—in one place is key to being able to stay ahead of things like brute force account compromise in the cloud.
Tawnya Lancaster joined AT&T Security as a Senior Product Marketing Manager in 2018. Previously, she served as the Director of Global Communications for Skybox Security, where she specialized in cybersecurity thought leadership for the vulnerability and threat management and firewall and security policy management space. She graduated from Oregon State University with a B.A. in English, and has received certification in Stanford’s Professional Publishing course, an intensive program for established publishing and communication professionals.
This guest blog is part of a Channel Futures sponsorship
Read more about:
MSPsAbout the Author
You May Also Like


